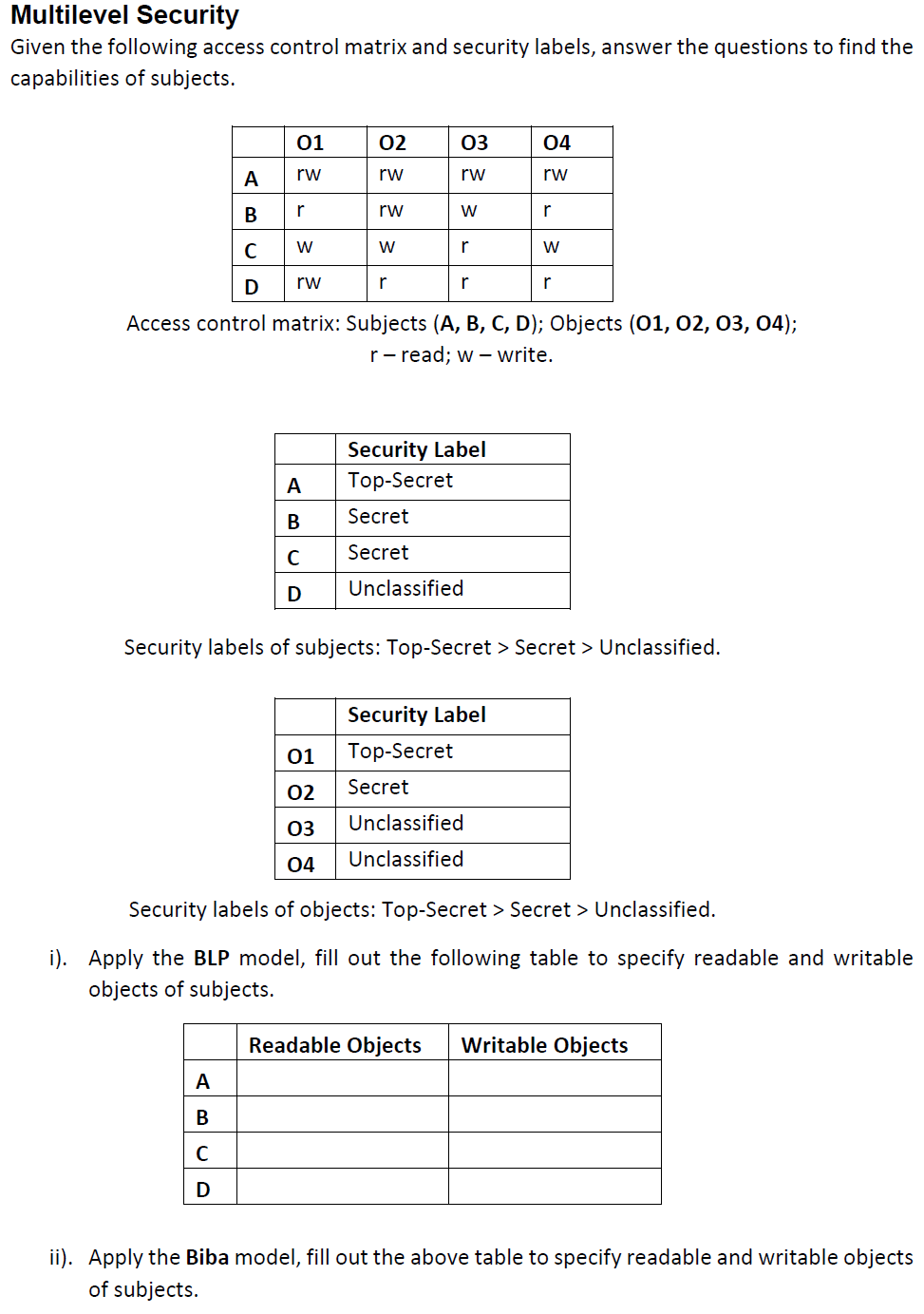
40 security labels access control
Using Security Labels for Directory Access and Replication Control - Isode The access control model is that a Security Label is associated with each entry in the directory, and that label indicates the sensitivity of the information contained in the directory entry. The example DIT "organizations", with different Security Labels. 3 Reasons Why Access Control System is Important in Business Having the ability to control access at any point in time is critically essential for security, safety, and health workers. So, an organization can...
› blog › the-role-of-accessThe Role of Access Control in Information Security Nov 12, 2020 · The next type of access model is known as attribute-based access control (ABAC). According to NIST: “It represents a point on the spectrum of logical access control from simple access control lists to more capable role-based access, and finally to a highly flexible method for providing access based on the evaluation of attributes.”
Security labels access control
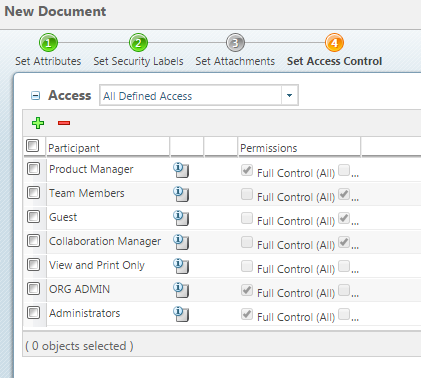
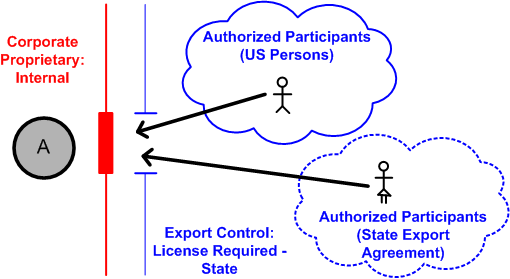
Products - Red Hat Customer Portal Engage with our Red Hat Product Security team, access security updates, and ensure your environments are not exposed to any known security vulnerabilities. ... Share, secure, distribute, control, and monetize your APIs on an infrastructure platform built for performance, customer control, and future growth. Product Documentation Product Info ... Security Labels and Access Control - support.ptc.com To access an object, a user must be cleared for all security labels, either as an authorized participant or by an active agreement, and have proper access control permissions for that object. The following flow chart provides an overview of how Windchill processes security labels and access control to grant or deny a user access to an object. Access control for projects with IAM - Google Cloud Oct 26, 2022 · Using predefined roles. IAM predefined roles allow you to carefully manage the set of permissions that your users have access to. For a full list of the roles that can be granted at the project level, see Understanding Roles. The following table lists the predefined roles that you can use to grant access to a project.
Security labels access control. access.redhat.com › productsProducts - Red Hat Customer Portal Infrastructure and Management Red Hat Enterprise Linux. Red Hat Enterprise Linux (RHEL) is the world's leading open source operating system that provides an intelligent, stable, and security-focused foundation for modern, agile business operations. Chapter 14. Security | FreeBSD Documentation Portal In some cases, system administration needs to be shared with other users. FreeBSD has two methods to handle this. The first one, which is not recommended, is a shared root password used by members of the wheel group. With this method, a user types su and enters the password for wheel whenever superuser access is needed. The user should then type exit to leave … learn.microsoft.com › en-us › microsoft-365Search the audit log in the Microsoft Purview compliance ... Oct 03, 2022 · For more information about the operations that are audited in each of the services listed in the previous table, see the Audited activities section in this article.. The previous table also identifies the record type value to use to search the audit log for activities in the corresponding service using the Search-UnifiedAuditLog cmdlet in Exchange Online PowerShell or by using a PowerShell script. Access Control for Property Graph Data (Graph-Level and OLS) Oracle Graph supports two access control and security models: graph level access control, and fine-grained security through integration with Oracle Label Security (OLS). Graph-level access control relies on grant/revoke to allow/disallow users other than the owner to access a property graph.
California Senate Blocks Mandatory ID Implants - Security Sales ... SACRAMENTO — The California state Senate passed legislation that would bar employers from requiring workers to have identification devices implanted under their skin. State Sen. Joe Simitian (D-Palo Alto) proposed the measure after at least one company began marketing radio frequency identification (RFID) devices for use in humans. The devices, as small as a grain […] The Role of Access Control in Information Security Nov 12, 2020 · The next type of access model is known as attribute-based access control (ABAC). According to NIST: “It represents a point on the spectrum of logical access control from simple access control lists to more capable role-based access, and finally to a highly flexible method for providing access based on the evaluation of attributes.” cloud.google.com › docs › access-control-projAccess control for projects with IAM | Resource Manager ... Oct 12, 2022 · IAM lets you adopt the security principle of least privilege, so you grant only the necessary access to your resources. IAM lets you control who (users) has what access (roles) to which resources by setting IAM policies, which grant specific roles that contain certain permissions. Access Control using Security Labels & Security Clearance - Isode Security Labels and Security Clearance provides a mechanism for controlling access to information that works well for large numbers of users. It can be an effective approach for access control in organizations that do not use non-electronic security labels. The following diagram shows the translation of the earlier example into electronic form.
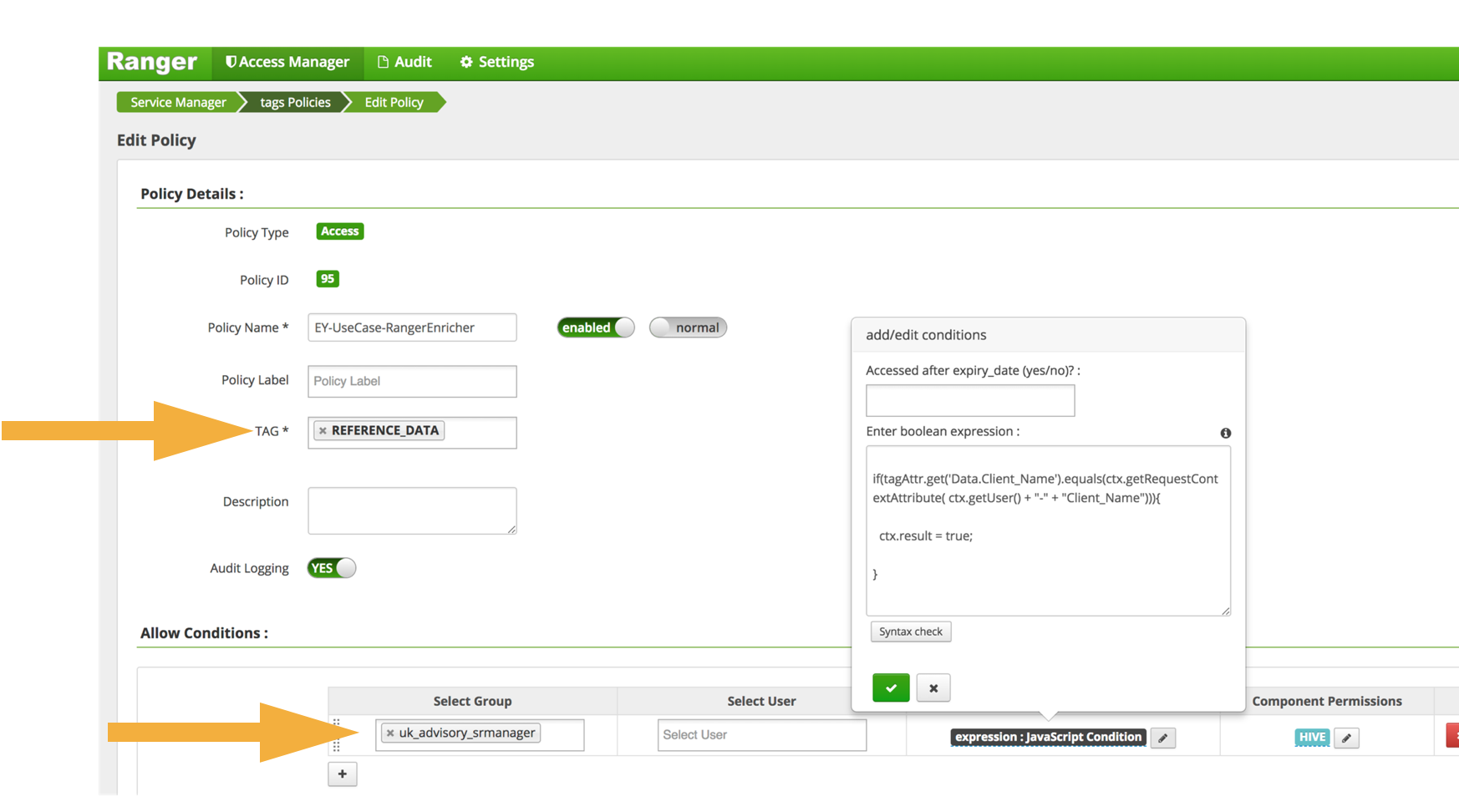
Security-labels - FHIR v4.3.0 - Health Level Seven International A security label is a concept attached to a resource or bundle that provides specific security metadata about the information it is fixed to. The Access Control decision engine uses the security label together with any provenance resources associated with the resource and other metadata (e.g. the resource type, resource contents, etc.) to. approve read, change, and other operations Cellotape | NFC & RFID Label Solutions | San Francisco At Resource Label Group we are here to help you find answers to your label and packaging challenges. With a network of locations and years of expertise we are up to the task! If you prefer, please call us at 1.888. 526.8177 or click below to chat with us (M-F 8 am - 5 pm Central). en.wikipedia.org › wiki › Mandatory_access_controlMandatory access control - Wikipedia Sun's Trusted Solaris uses a mandatory and system-enforced access control mechanism (MAC), where clearances and labels are used to enforce a security policy. However note that the capability to manage labels does not imply the kernel strength to operate in multilevel security mode [ citation needed ] . Label Security | Oracle Oracle Label Security Control what data users see based on data and session labels. Oracle Label Security records and enforces access permission for data based on project codes, regions, or data classifications. These controls reduce the risk of unauthorized access to sensitive data and help to demonstrate regulatory compliance.
Gerrit Code Review - Access Controls - Google Open Source It is somewhat common to create two groups at the same time, for example Foo and Foo-admin, where the latter group Foo-admin owns both itself and also group Foo.Users who are members of Foo-admin can thus control the membership of Foo, without actually having the access rights granted to Foo.This configuration can help prevent accidental submits when the members of …
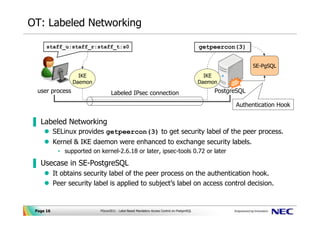
How security labels control access - help.hcltechsw.com You can encrypt data, secure connections, control user privileges and access, and audit data security. Security in HCL OneDB™ These topics document methods for keeping your data secure by preventing unauthorized viewing and altering of data or database objects, including how to use the secure-auditing facility of the database server.
Access control - Wikipedia In the fields of physical security and information security, access control (AC) is the selective restriction of access to a place or other resource, while access management describes the process.The act of accessing may mean consuming, entering, or using. Permission to access a resource is called authorization.. Locks and login credentials are two analogous mechanisms …
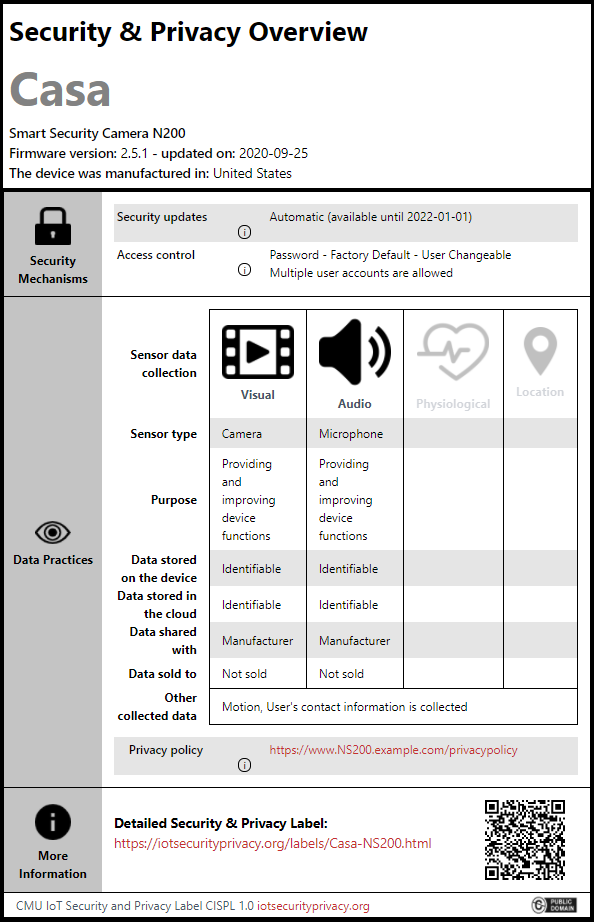
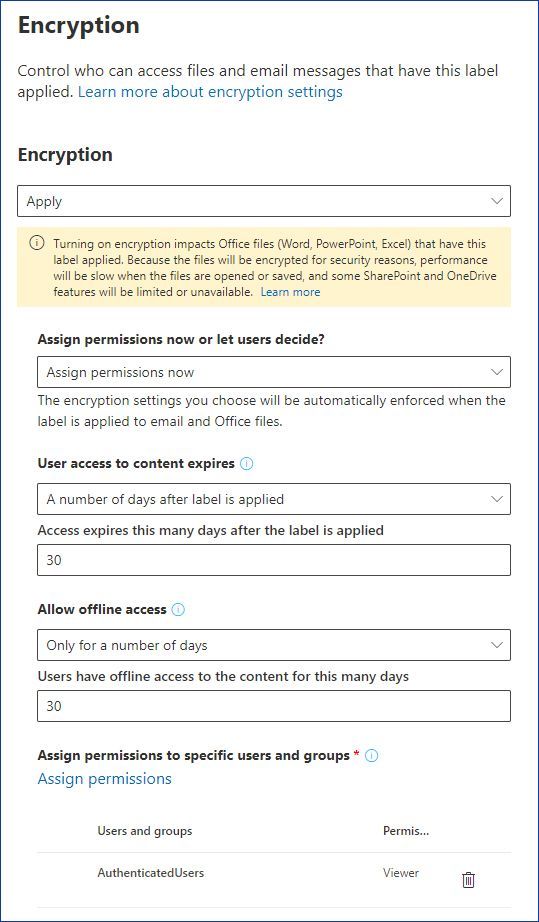
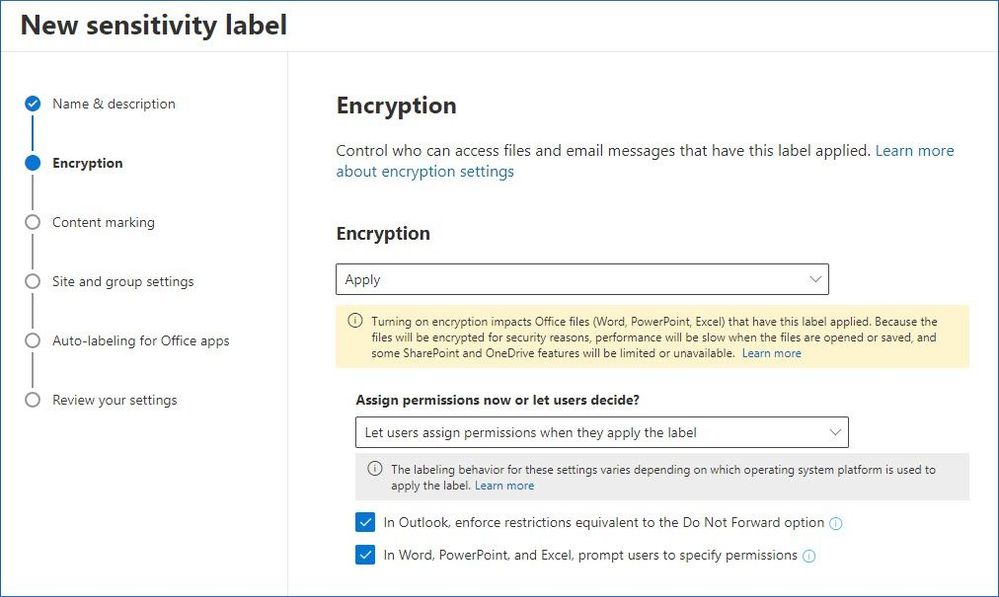
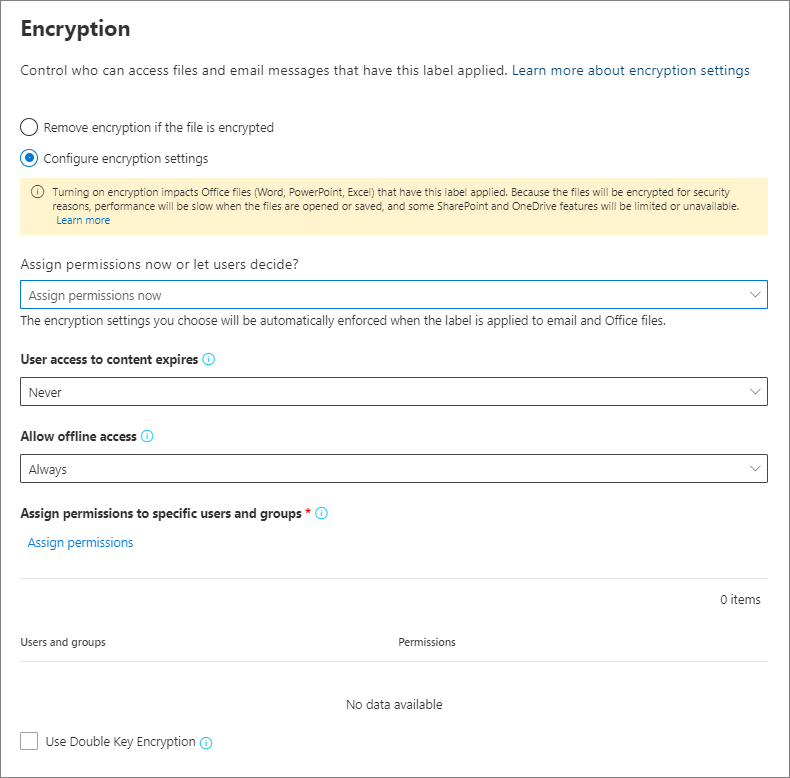
Apply encryption using sensitivity labels - Microsoft Purview ... Oct 03, 2022 · Only labels that are configured to assign permissions now support different values for offline access. Labels that let users assign the permissions automatically use the tenant's Rights Management use license validity period. For example, labels that are configured for Do Not Forward, Encrypt-Only, and prompt users to specify their own permissions.
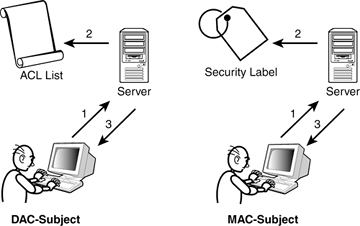
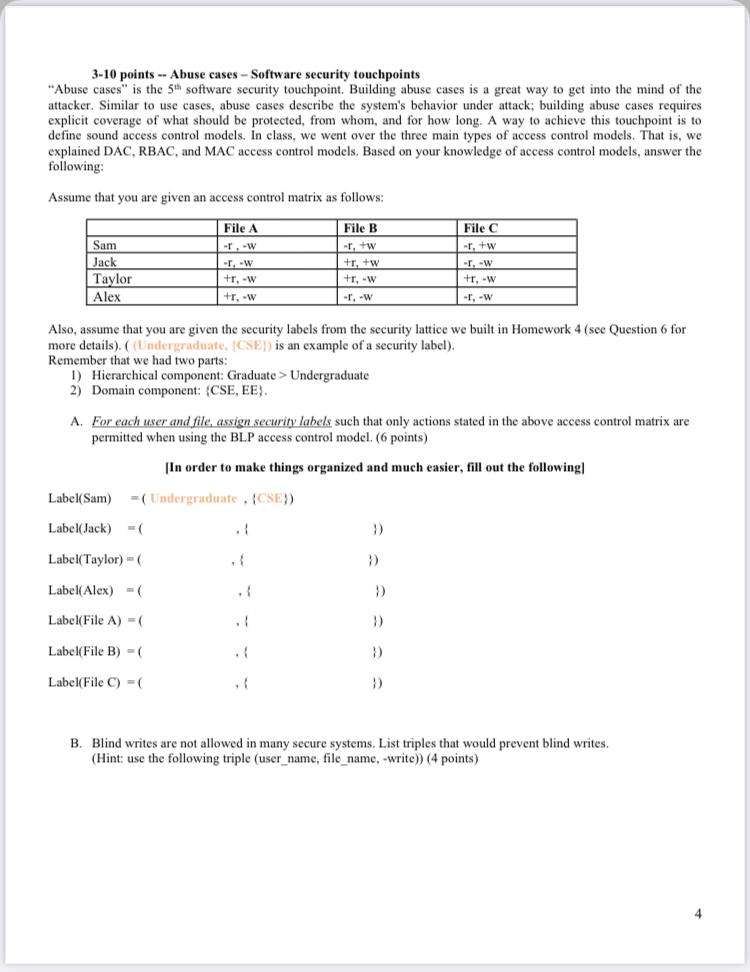
Mandatory access control - Wikipedia In computer security, mandatory access control (MAC) refers to a type of access control by which the operating system or database constrains the ability of a subject or initiator to access or generally perform some sort of operation on an object or target. In the case of operating systems, a subject is usually a process or thread; objects are constructs such as files, directories, …
Search the audit log in the Microsoft Purview compliance portal ... Oct 03, 2022 · For more information about the operations that are audited in each of the services listed in the previous table, see the Audited activities section in this article.. The previous table also identifies the record type value to use to search the audit log for activities in the corresponding service using the Search-UnifiedAuditLog cmdlet in Exchange Online …
docs.freebsd.org › en › booksChapter 14. Security | FreeBSD Documentation Portal See the section titled "Remote administration" in info heimdal for details on designing access control lists. Instead of enabling remote kadmin access, the administrator could securely connect to the KDC via the local console or ssh(1) , and perform administration locally using kadmin -l .
How security labels control access Label-based access control (LBAC) works by comparing the labels that you have associated with users against labels that you have associated with data by using a predefined rule set (IDSLBACRULES). You construct these labels with security label components, which represent different levels of data classification and access authority.
en.wikipedia.org › wiki › Access_controlAccess control - Wikipedia The term access control refers to the practice of restricting entrance to a property, a building, or a room to authorized persons. Physical access control can be achieved by a human (a guard, bouncer, or receptionist), through mechanical means such as locks and keys, or through technological means such as access control systems like the mantrap ...
Label-based access control (LBAC) overview - IBM In label-based access control (LBAC) a security label is a database object that describes a certain set of security criteria. Security labels are applied to data in order to protect the data. They are granted to users to allow them to access protected data. Format for security label values
[Knowledge Hub] Windchill PLM Permissions/Access Control/Security Label How to set up security labels? How to troubleshoot access control issues? Log in eSupport Login: Close: Username (Email Address) Password; Invalid username or password Cancel: Forgot password? Create a new account: Support ... Windchill PLM Permissions/Access Control/Security Label Modified: 17-Oct-2022 Applies To Windchill PDMLink 10.0 to 12.0 ...
How security labels control access - ibm.com Security labels rely on security label components to store information about the classification of data and about which users have access authority. Label-based access control (LBAC) works by comparing the labels that you have associated with users against labels that you have associated
Access Control Security Systems in Fremont, CA A panel that manages the access control barrier. A structure that connects and communicates with these components and links the ACS with reaction elements. Access control barriers in Fremont are physical devices that could be drop or wedge arm barriers, turnstiles, portals or facilities for guards. Verification equipment might be a card reader ...
Learn about sensitivity labels - Microsoft Purview (compliance) Oct 14, 2022 · Labels can be published to any specific user or email-enabled security group, distribution group, or Microsoft 365 group (which can have dynamic membership) in Azure AD. Specify a default label for unlabeled documents and emails, new containers (when you've enabled sensitivity labels for Microsoft Teams, Microsoft 365 groups, and SharePoint ...
How security labels control access - help.hcltechsw.com You can encrypt data, secure connections, control user privileges and access, and audit data security. Security in HCL OneDB™ The HCL OneDB™ Security Guide documents methods for keeping your data secure by preventing unauthorized viewing and altering of data or database objects, including how to use the secure-auditing facility of the ...
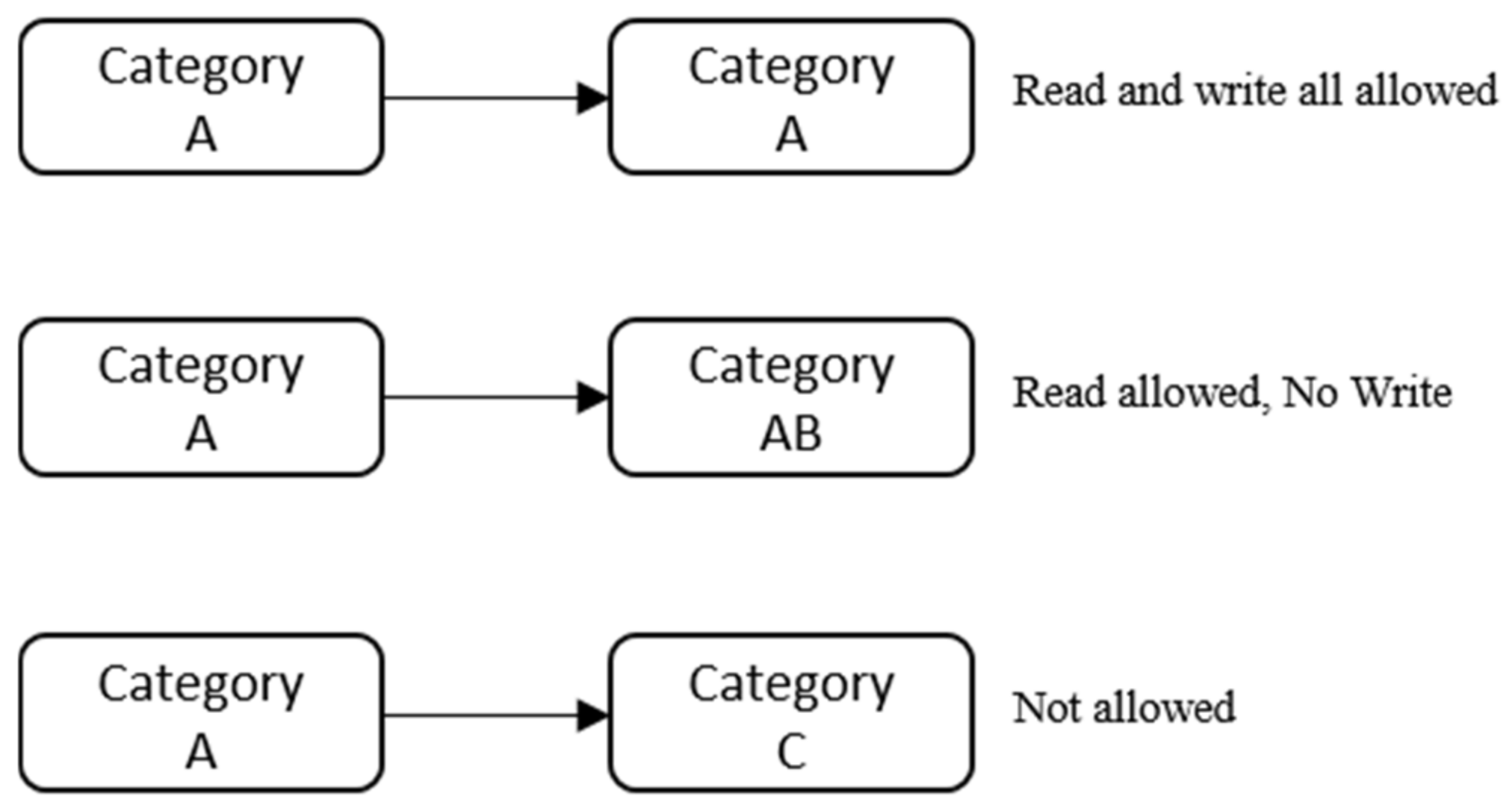
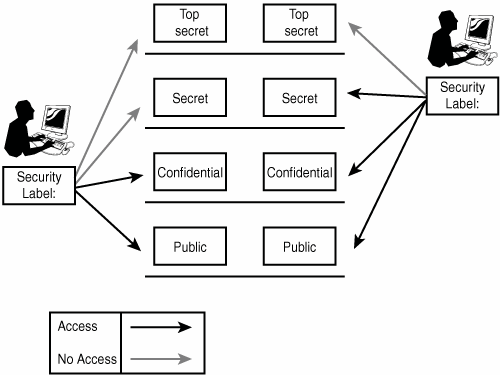
Access Control Models: MAC, DAC, RBAC, & PAM Explained MAC works by applying security labels to resources and individuals. These security labels consist of two elements: Classification and clearance — MAC relies on a classification system (restricted, secret, top-secret, etc.) that describes a resource's sensitivity. Users' security clearances determine what kinds of resources they may access.
Access control for projects with IAM - Google Cloud Oct 26, 2022 · Using predefined roles. IAM predefined roles allow you to carefully manage the set of permissions that your users have access to. For a full list of the roles that can be granted at the project level, see Understanding Roles. The following table lists the predefined roles that you can use to grant access to a project.
Security Labels and Access Control - support.ptc.com To access an object, a user must be cleared for all security labels, either as an authorized participant or by an active agreement, and have proper access control permissions for that object. The following flow chart provides an overview of how Windchill processes security labels and access control to grant or deny a user access to an object.
Products - Red Hat Customer Portal Engage with our Red Hat Product Security team, access security updates, and ensure your environments are not exposed to any known security vulnerabilities. ... Share, secure, distribute, control, and monetize your APIs on an infrastructure platform built for performance, customer control, and future growth. Product Documentation Product Info ...























Post a Comment for "40 security labels access control"